Global police operation disrupts aggressive “Game Over Zeus” & the “Cryptolocker virus”
Internet users have two-week window to protect themselves, says UK’s National Crime Agency after working with Europol and FBI
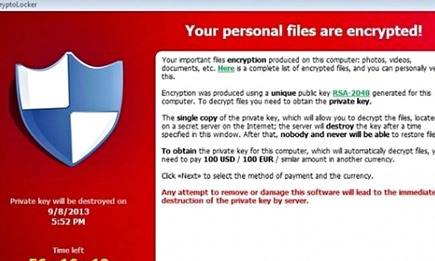 Cryptolocker will encrypt files with a public key that is widely seen as unbreakable
Cryptolocker will encrypt files with a public key that is widely seen as unbreakable
US authorities named Russian national Evgeniy Bogachev as the face of a malicious software scheme responsible for stealing millions from people around the world, after a successful campaign to disrupt two major computer networks.
Digital police from across the globe announced they had seized control over the weekend of two computer networks that had been used to steal banking information and ransom information locked in files on infected computers. But they warned people with infected computers to take action now to prevent further attacks.
US and European officials announced they had managed to crack the malicious software (malware) known as Gameover Zeus that had been used to divert millions of dollars to bank accounts of criminals. The authorities have also cracked Cryptolocker – a viral scam that shutout hundreds of thousands of users from their own computers and ransomed the data.
The UK’s National Crime Agency (NCA) told British victims that they have a two-week window to protect themselves, after working with the FBI, Europol and other law enforcement bodies to temporarily seize control of the global network of infected computers.
The US authorities identified Bogachev, of Anapa in the Russian Federation, as Gameover Zeus’s main administrator. At a press conference, deputy attorney general James Cole called him “a true 21st-century criminal who commits cyber-crimes across the globe with the stroke of a key and the click of a mouse …These crimes have earned Bogachev a place on its list of the world’s most-wanted cyber criminals.”
According to the FBI’s “cyber most wanted” list Bogachev has been using variants of the Zeus malware since 2009 and communicates using the online monikers “lucky12345” and “slavik”. Gameover Zeus (GOZ) started appearing in 2011 and is believed to be “responsible for more than one million computer infections, resulting in financial losses in the hundreds of millions of dollars”.
“He is known to enjoy boating and may travel to locations along the Black Sea in his boat,” according to the FBI.
The Cryptolocker software locked PC users out of their machines, encrypting all their files and demanding payment of one Bitcoin (currently worth around £300, or $650) for decryption.
It’s believed Cryptolocker, which the FBI estimated acquired $27m in ransom payments in just the first two months of its life, has infected more than 234,000 machines.
A chief suspect from Russia has been identified, but is still at large, Troels Oerting, head of Europol’s European Cyber Crime Centre (EC3) told the Guardian. He said other arrests related to the operation were “in progress”.
The global effort to stop the spread of the Cryptolocker ransom-ware has focused on its delivery method, GOZ. The malware connected infected machines by peer-to-peer connections – in theory making it harder for the authorities to track and stop.
GOZ was designed to steal people’s online banking login details, who were usually infected by clicking on attachments or links in emails that looked innocuous. However, it also dropped Cryptolocker on their computers.
“Nobody wants their personal financial details, business information or photographs of loved ones to be stolen or held to ransom by criminals,” said Andy Archibald, deputy director of the NCA’s National Cyber Crime Unit.
“By making use of this two-week window, huge numbers of people in the UK can stop that from happening to them. Whether you find online security complicated or confusing, or simply haven’t thought about keeping your personal or office computers safe for a while, now is the time to take action.”
Affected users are being advised to update their operating system software and security software, and also to “think twice before clicking on links or attachments in unsolicited emails”.
Not-for-profit body Get Safe Online has worked with the NCA to launch a dedicated section of its website to provide guidance and tools, although at the time of publication the website appeared to be offline.
Behind the scenes, the law enforcement groups have been taking over points of control in GOZ’s peer-to-peer network: an action known as “sinkholing” in the security world. By doing this, they have been able to cut off criminal control over the infected computers.
Dismantling peer-to-peer operated malware is difficult, but it has been done before: for example one case of a data-stealing virus called ZeroAccess, which infected as many as 1.9m PCs in 2013.
In that case, security researchers from Symantec managed to send lists of fake peers to infected machines, which meant they could no longer receive commands from the controllers of the malicious network, known as a botnet.
Symantec researchers said today that key nodes in GOZ’s network had been disabled, along with a number of the domains used by the attackers.
Oerting told The Guardian the entire GOZ’s operations infrastructure had been sinkholed, meaning the malware should “not reappear for … considerable time”.
Although arrests have not yet been made, Oerting believes the eventual impact will be “great”. “[It will not last] forever, but the infrastructure is gone and the criminals will have to build and distribute from scratch,” he added.
Foxnwolf comments…….
Internet banking is still safe as long as you Think About What You Do Online
1. Make Sure that your virus security is up to date on your machine
2. Make Regular backups (DO ONE NOW)
3. Do Not go on websites that your not sure about
4. Do Not download anything unless you know what your doing and that the content is safe. And when you use a memory stick from an unknown source open it via your machines security software. Dont just double-click it and hope for the best
5. Keep Away from “Peer to Peer” (sharing) torrents / websites unless you know what you are doing
6. Download “Rapport” its a free browser security software. Useful initially for banking / online payments, but use it for any other site you go on. It sits on your browser bar and when you go on any site you usually use just click the icon and click on “Protect this Site” Whether a banking site or not. It will also tell you if your on a mirror and \ or hookey site and prevent the connection going further
7. If You receive an email and you dont know who its from and \ or you dont recognize the text in the subject line, dont even open it. Just single click on it to “mark \ highlight” it and send it to the spam box (dont open in the spam box either, leave it alone and dont go to have a peek at the script unless you know how to do this)
8. Always Log-out of a site that you had to log in to (wait for the confirmation window that your logged out). Never just Close the browser / window. That is Deadly
9. Make Sure that your WiFi security at Home \ Business etc has a proper password not the standard open ended password it sometimes comes with otherwise anyone has a pathway to your machine(s). (PC`s, Mac`s, iPad, iPhone or any other phone or device on your system (even your smart TV can be monitored) And so can your webcam (Keep this off altogether unless your actually using it)
10. Finally, Change your online payment password(s) every 6 or 12 mths
Pass this around your family and friends…







